Introduction#
FortiGate’s web filtering security profile allows to control which websites users can access. Nowadays, most of the user traffic to the internet is encrypted. However, FortiGate’s SSL Deep Inspection can be leveraged to expand the visibility of encrypted traffic traversing the firewall, allowing to enforce security profiles like web filtering with more granularity.
This article explains when SSL Deep Inspection should be used for accurate web filtering and provides guidance on how to enable it.
HTTP (unencrypted) Web Navigation#
When accessing a HTTP site (unencrypted), the application layer information traverses unencrypted between the client and the web server. For example, a client trying to access http://example.com/
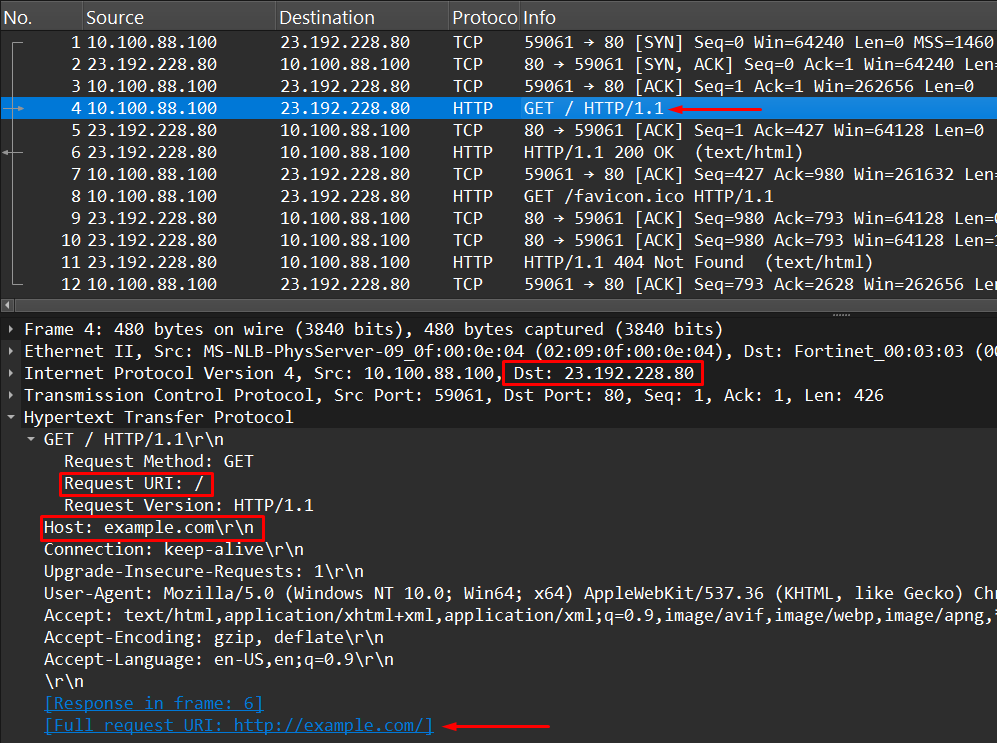
Running a network sniffer between the client and the server when the client is connecting to the website provides useful information when troubleshooting:
- Destination IP:
23.192.228.80 - Protocol:
HTTP - HTTP information:
- Host:
example.com - Request URI:
/ - Request Method:
GET
- Host:
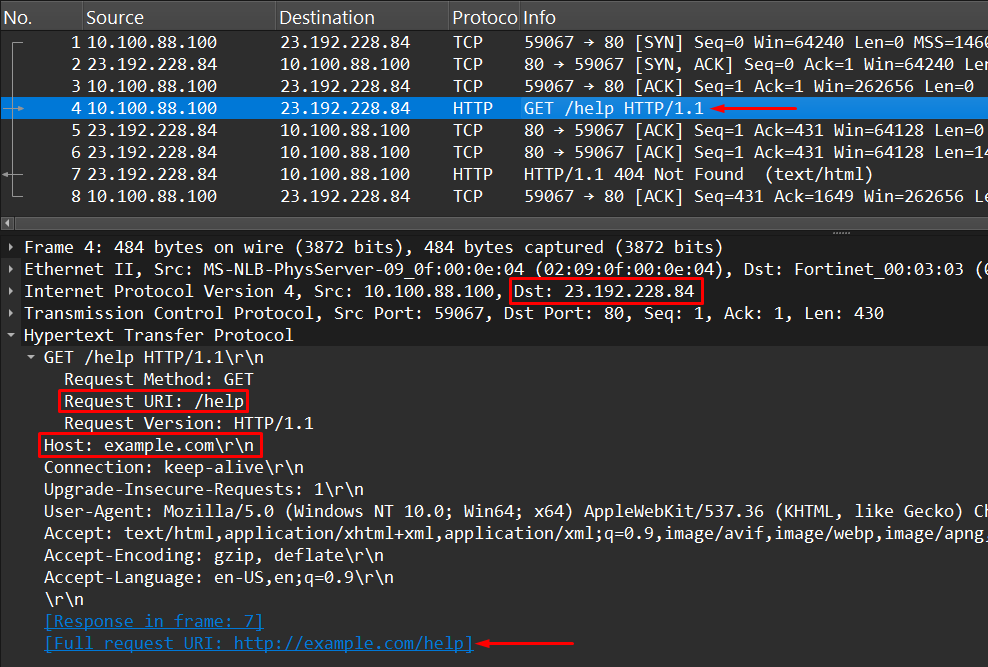
If the user then visits http://example.com/help , the sniffed traffic would reflect the new requested URI:
- Destination IP:
23.192.228.84 - Protocol:
HTTP - HTTP information:
- Host:
example.com - Request URI:
/help<————– - Request Method:
GET
- Host:
Configuring a Web Filter Security Profile#
To restrict user access to website categories or specific websites a web filter profile is defined and applied on a firewall policy.
For example, to restrict access to a specific URI example.com/help, the following steps can be followed on FortiGate’s GUI:
- Go to
Security Profiles > Web Filter - Select
Create Newto create a new web filter profile or edit an existing one. - Set a name to the profile.
- Disable
FortiGuard Category Based Filtersince web filtering based on the site category (e.g. phishing, advertising, games, business, etc. ) won’t be applied. - Under
Static URL Filter, enableURL Filterswitch, then selectCreate New:
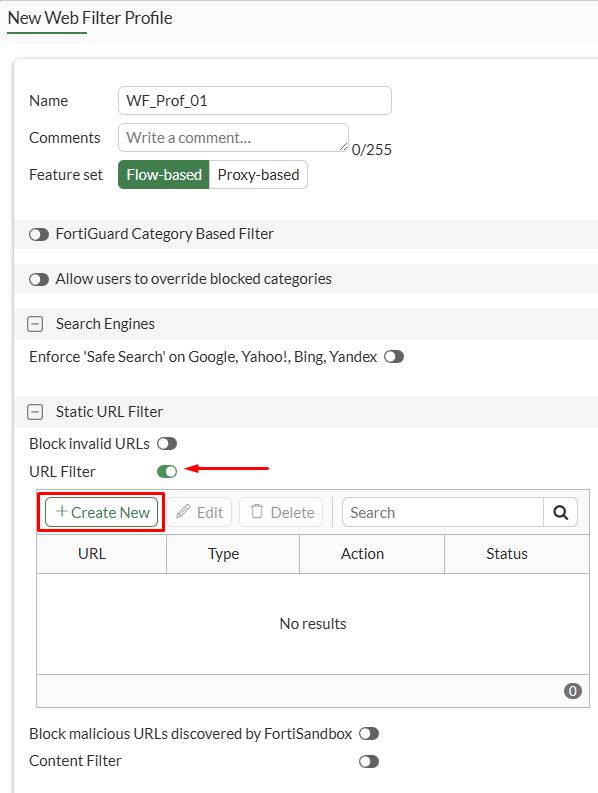
- Specify the desired URL
example.com/help, theBlockaction and clickOK:
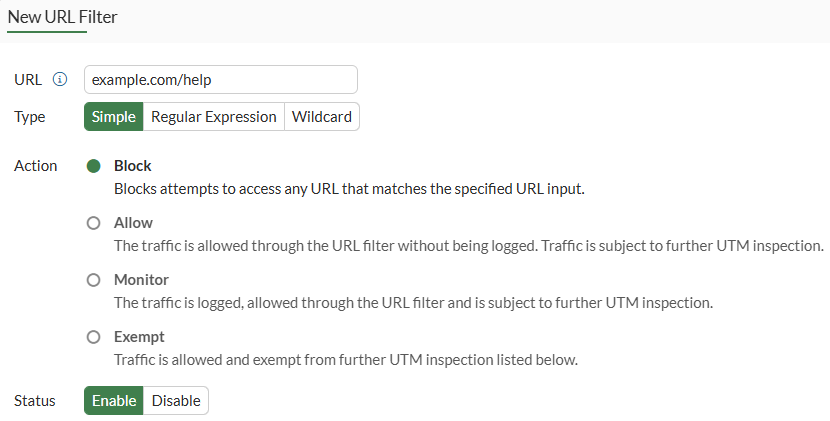
- Verify the entry is created, then select
OK:
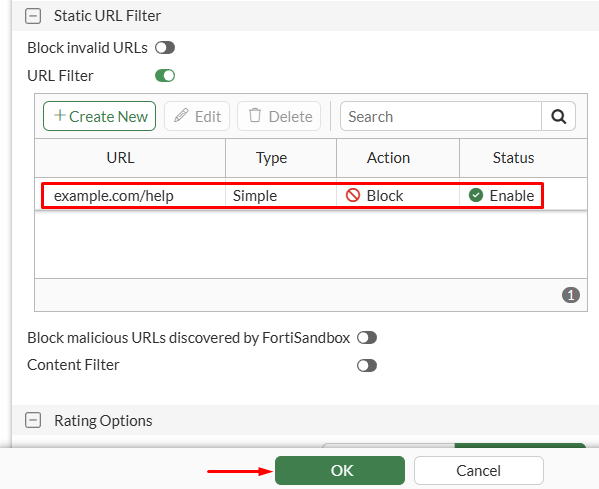
The web filter profile is now ready to be applied on a firewall policy under Policy & Objects > Firewall Policy.
Restrict URL access for HTTP#
When using web filtering together with HTTP protocol, an SSL inspection profile is not required to be applied on the policy, since HTTP is an unencrypted protocol. By default, the firewall will be able to inspect the L7 content of HTTP packets, like the Host and URL values in the HTTP header.
Following the proposed example to block the access to example.com/help, a firewall policy can be created, defining the user IP address as source and using the no-inspection SSL profile together with the recently created web filter profile.
- Navigate to
Policy & Objects > Firewall Policy. - Define the matching conditions for the user traffic to the internet.
- Under
Security Profilessection, select the created web filter profile and the no-inspection SSL inspection profile:
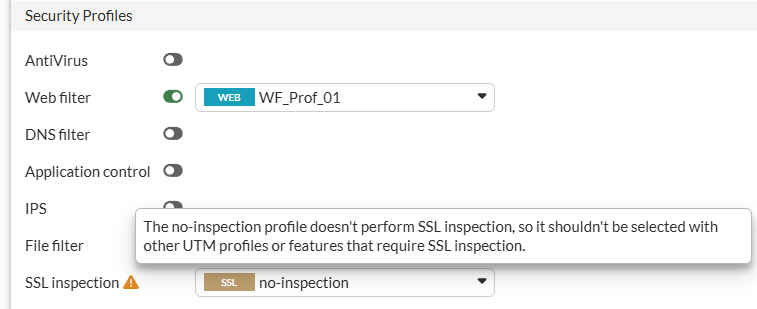
The result of this configuration is that when the user tries to access http://example.com/help, the web filter profile takes action and blocks the site access, showing the following block message to the user:
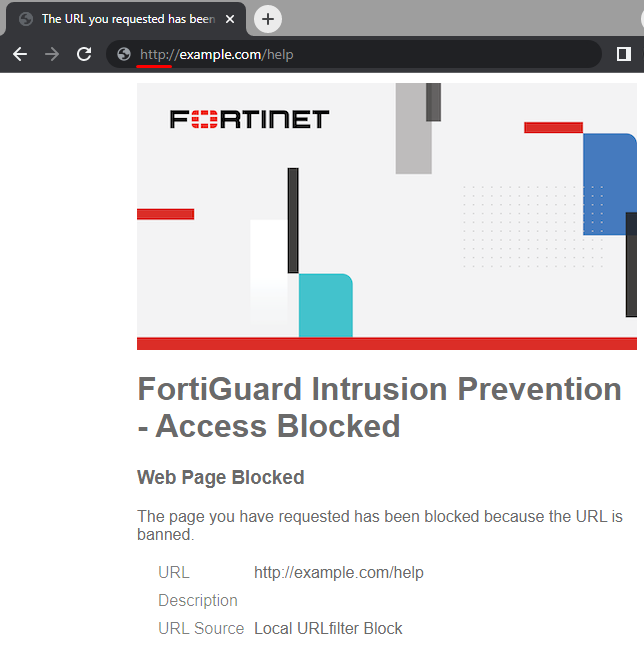
The URL value shown in the block page accordingly matches the requested URL.
The traffic logs (Log & Report > Forward Traffic) indicate a deny because of UTM:
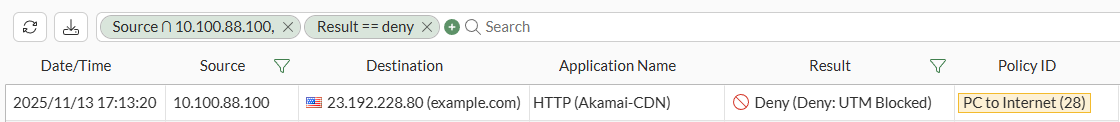
Double clicking on this log it can be verified under the Security tab that the requested URL http://example.com/help was blocked by the web filter profile, using the Local URL filter Block:
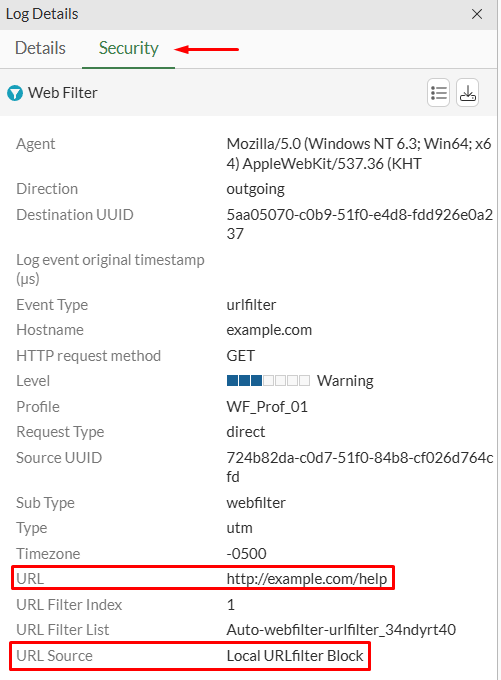
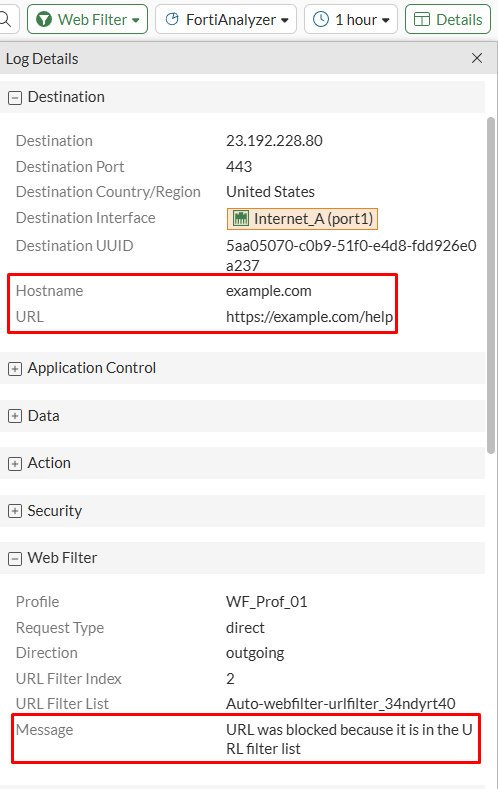
More details regarding the web filtering event can be reviewed under Log & Report > Security Events > Web Filter:
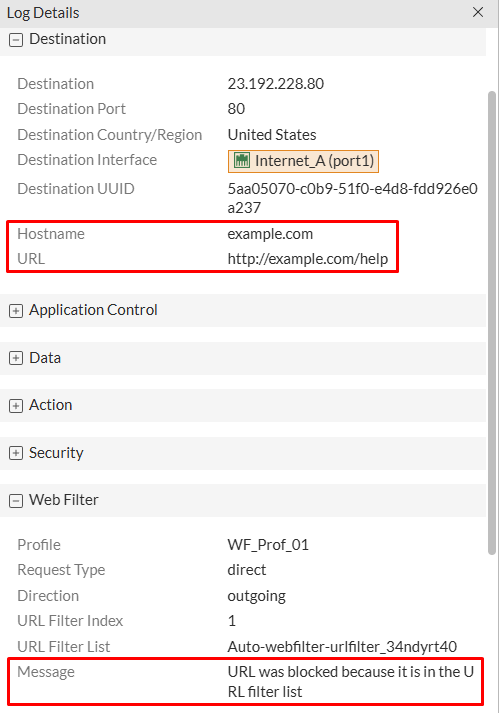
Here the Hostname, and URL values are confirmed, as well as the message regarding the block of the Web Filter: “URL was blocked because it is in the URL filter list”.
HTTPS (encrypted) Web Navigation#
When accessing a HTTPS site, the application payload travels encrypted between the client and the server, safeguarding it from unauthorized eavesdropping, data tampering and man-in-the middle attacks.
A user trying to access https://example.com/help while running a sniffer between the client and the server gives more understanding about the communication when HTTPS is used:
The packet capture shows the following:
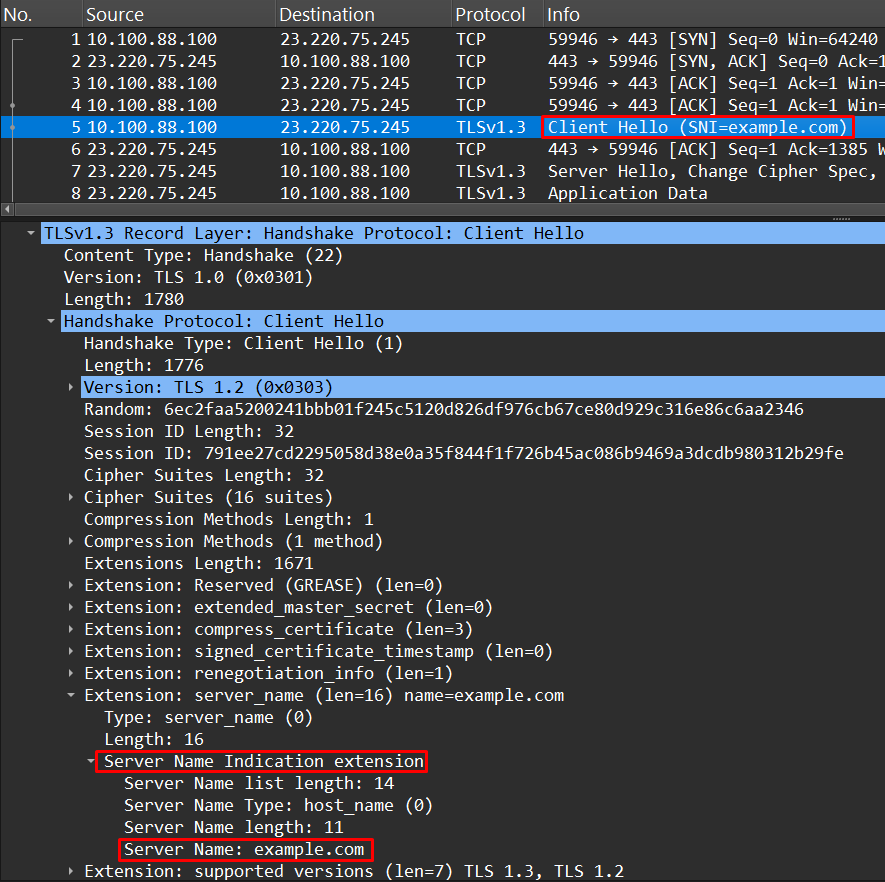
The screenshot shows the details in the first application data packet (TLS) from the client, which is a TLS Client Hello. The domain can be identified in the Server Name Indication (SNI) field: “Server Name: example.com”
When using no-inspection or certificate-inspection SSL profiles on FortiGate, FortiGate won’t be able to see the full requested URL. Only the domain name on the SNI field will be identified.
In practice, when traffic is encrypted (HTTPS) and the firewall policy is using certificate-inspection SSL profile, the Web Filter profile could only allow/block based on domains (e.g. https://example.com), and not domains plus URLs (e.g. https://example.com/help).
Restrict URL access for HTTPS#
The previous configuration of the web filter profile remains the same.
The firewall policy in place is modified to use the certificate-inspection SSL profile instead of the no-inspection SSL profile:
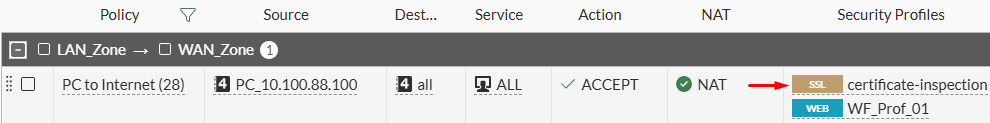
This time, the user will be able to access https://example.com/help without any restrictions from the firewall:

Now, the currently applied web filter profile is modified by changing the URL entry from example.com/help to example.com:
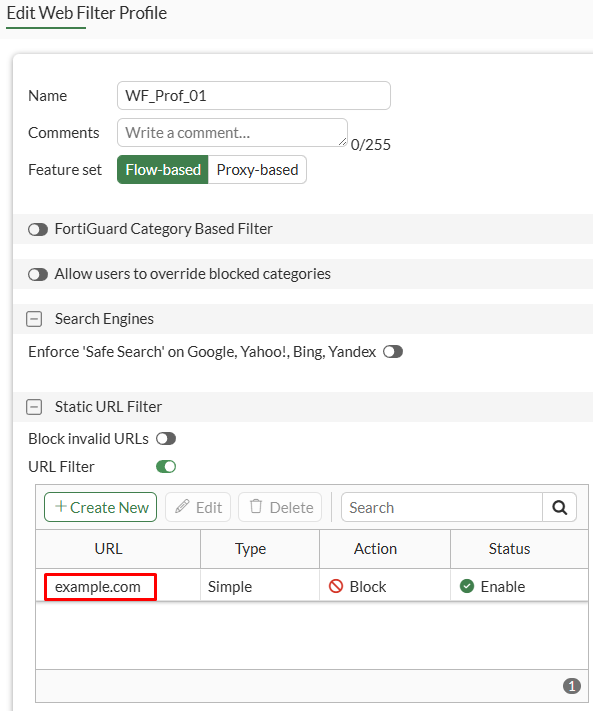
If the user tries to access https://example.com/help again, the page would be blocked this time:
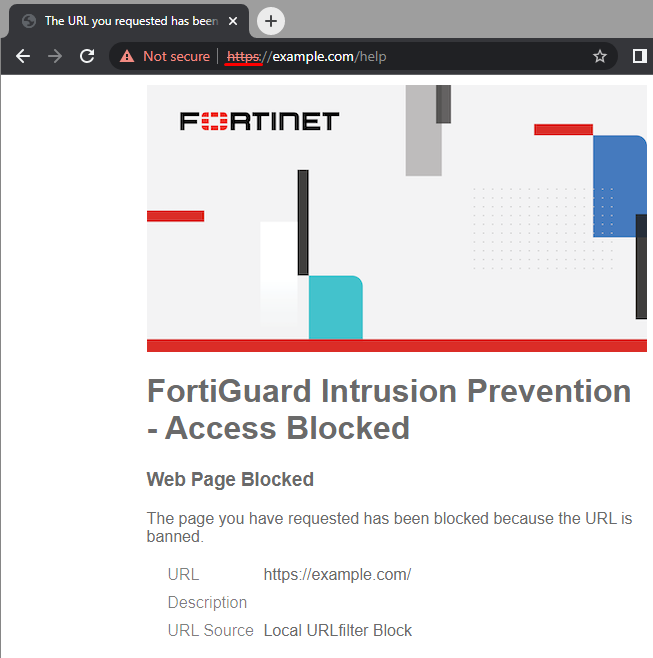
As a final test, return the web filter profile to the previous configuration where the only block entry was example.com/help:

Next, change the firewall policy SSL inspection profile to the default deep-inspection profile:
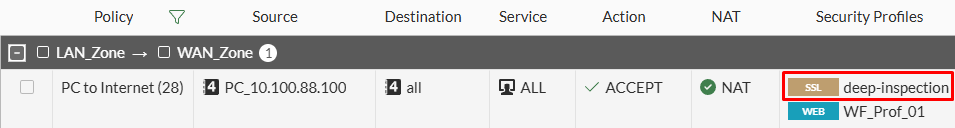
Using deep-inspection the accessed URL https://example.com/help is blocked by the web filter profile as desired:
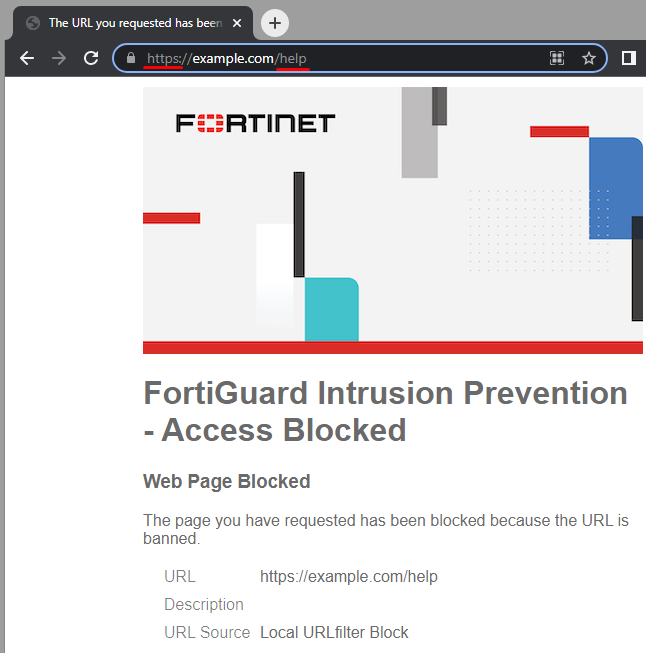
Compared to the previous test where the web filter profile was also blocking the URL example.com/help only but the SSL inspection profile was certificate-inspection, this time the configured URL was properly blocked.
Looking for this connection on traffic logs (Log & Report > Forward Traffic), the details under the Security tab indicate more information abut this block:
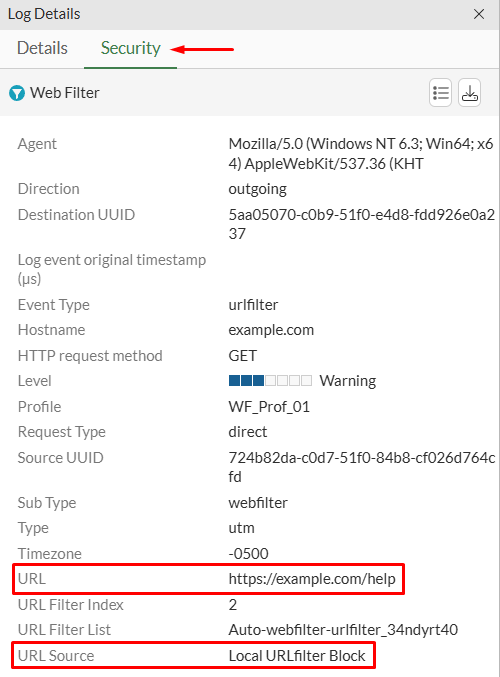
Under Log & Report > Security Events > Web Filter, complementary information about the block generated by the web filter profile are given:
Conclusion#
- When using HTTP, the no-inspection SSL profile can be used on the firewall policy together with a web filter to either block based on domain only (e.g. http://example.com) or based on a full URL (e.g. http://example.com/help).
- When using HTTPS, an SSL inspection security profile with Full SSL Inspection (like the default profile deep-inspection) is required to enforce static URL filtering based on complete URLs (e.g. https://example.com/help)
- When using HTTPS, an SSL inspection security profile with SSL Certificate Inspection (like the default profile certificate-inspection) is enough for enforcing static URL filtering based on domains (e.g. https://example.com).